Providing you the right technology and solutions to help secure, adapt and grow.
Today’s world challenges technology to solve almost everything and change is coming, whether organisations are prepared or not.
Secure Agility helps organisations deliver real transformation and take advantage of emerging technologies. Accelerate that path by partnering with a modern managed service provider (MSP) that offers integrated solutions, so you don’t have to deal with multiple parties.
Explore new ideas and business opportunities with a platform for innovation.
Don’t just endure change, drive it with digital.

Business Focus: Everything we do results in business improvement.
Reduced IT Opex: An MSP approach drives down operating and capital costs.
Streamlining: Be more efficient and do more with less equipment and resources. Get staff adding value.
Innovation: We establish a platform for growth and new ideas. Don't simply transform, be more innovative.
Business Security: Transformation should not result in more risk. We have a leading IT security practice

Over the years I've seen a lot of change in the technology industry, but what hasn't changed is how winning cultures always drive the best outcomes.
At Secure Agility, we've developed a fantastic mix of passion, technology and culture.
Let us help transform your organisation and empower your teams to succeed.

CEO, Secure Agility
Working with the Best
As a first-choice partner to some of Australia’s leading technology providers, we at Secure Agility take partnerships to the next level.
Our MSP model saves organisations costly integration work and we are accredited for ISO27001 and ISO22301 to provide you with the confidence to deal with a company that meets industry standards with routine audits.
We have achieved gold partner status with Telstra, Cisco and HPE, and have been Telstra Partner of the Year.

Our Technology Partners

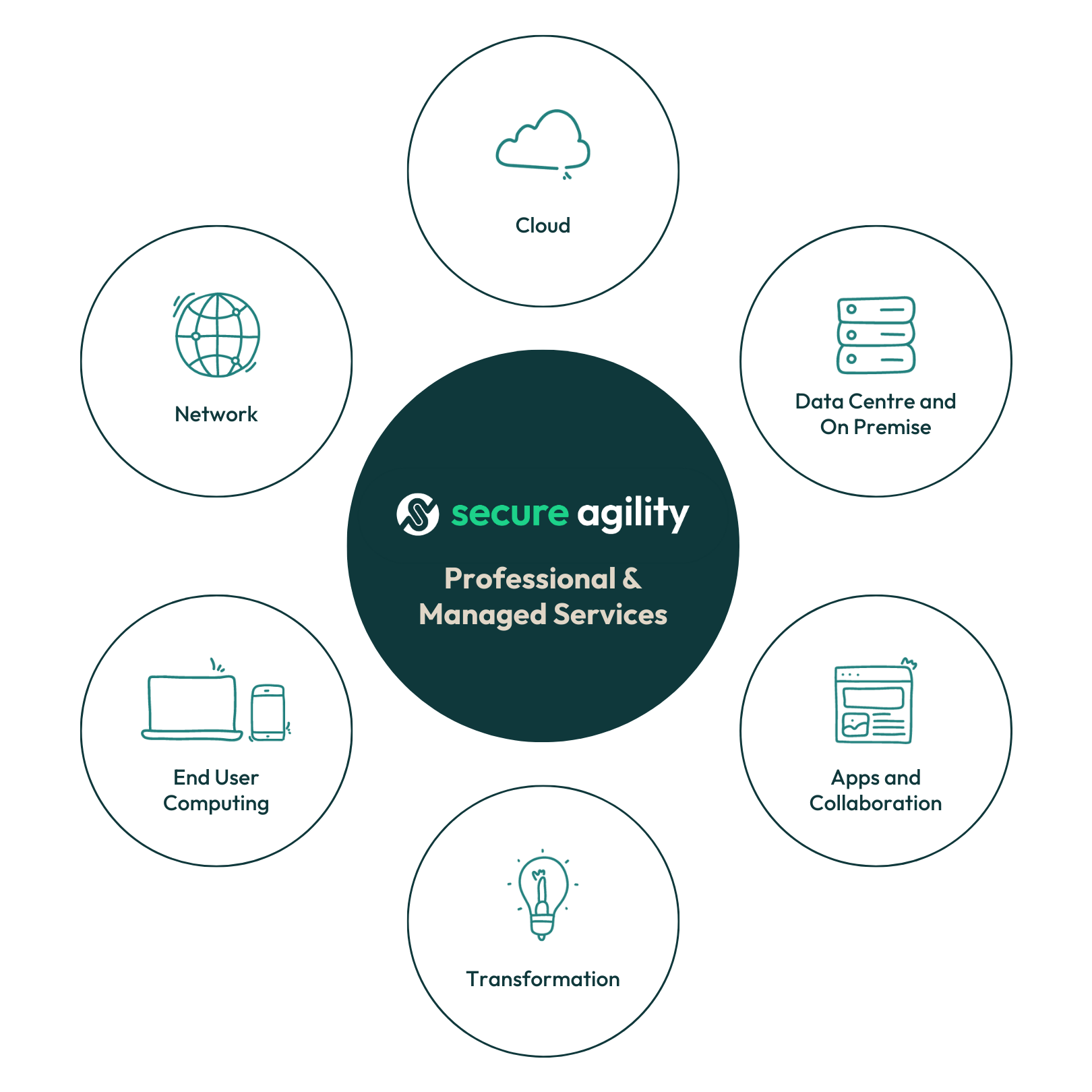
Four Pillars of Focus with secure support for your complete coverage
Professional and Managed ICT Solutions that just work
We focus on building robust and innovative solutions that enable you to achieve your desired outcomes. We provide integrated professional and managed services across the following core areas:
-
Network -
Cloud -
Data Centre and On Premise -
Apps and Collaboration -
End User Computing -
Transformation
Professional Services
Experienced technical and business consultants ready to inspire and support you in developing the right strategies to meet your business goals.
Managed Services
Proactive managed ICT services providing 24x7x365 management and monitoring of your environment, so your teams can focus on innovating.
Our consultants are here to help
Solve challenges
Workshop how to overcome challenges that stop you and your teams from achieving the outcomes you want.
Execute projects
You’ve got a strategy and plan; now you need someone to help you implement. Speak to us about how we can help you execute your project.
Turn ideas into reality
Change and innovation starts with an idea—we are the technology partner to help you turn your idea into a reality.
Trusted partner
If you’re looking for a new services partner or a fresh perspective to support your ICT strategy, we are the partner for you.
Our Approach
Here’s an overview of how we work and align with you
1. Discovery and Design
2. Build
3. Delivery
4. Handover
5. Managed Services
Meet our Technology Director & Founder - Charlie Tannous

![]()
Contact us today!
Complete your details and a specialist team member will get in touch.


