Tailored Solutions
We tailor our services to meet your business objectives
Help at every stage of your IT cyber security journey
Cybersecurity isn’t a one-time fix—it's an ongoing process of monitoring, detecting, responding, and planning. With Secure Agility's Secure360 services, we provide end-to-end protection, ensuring you’re always one step ahead of cyber threats.
Our proactive approach reduces the risk of disruption and strengthens your overall security posture.
Key Services:
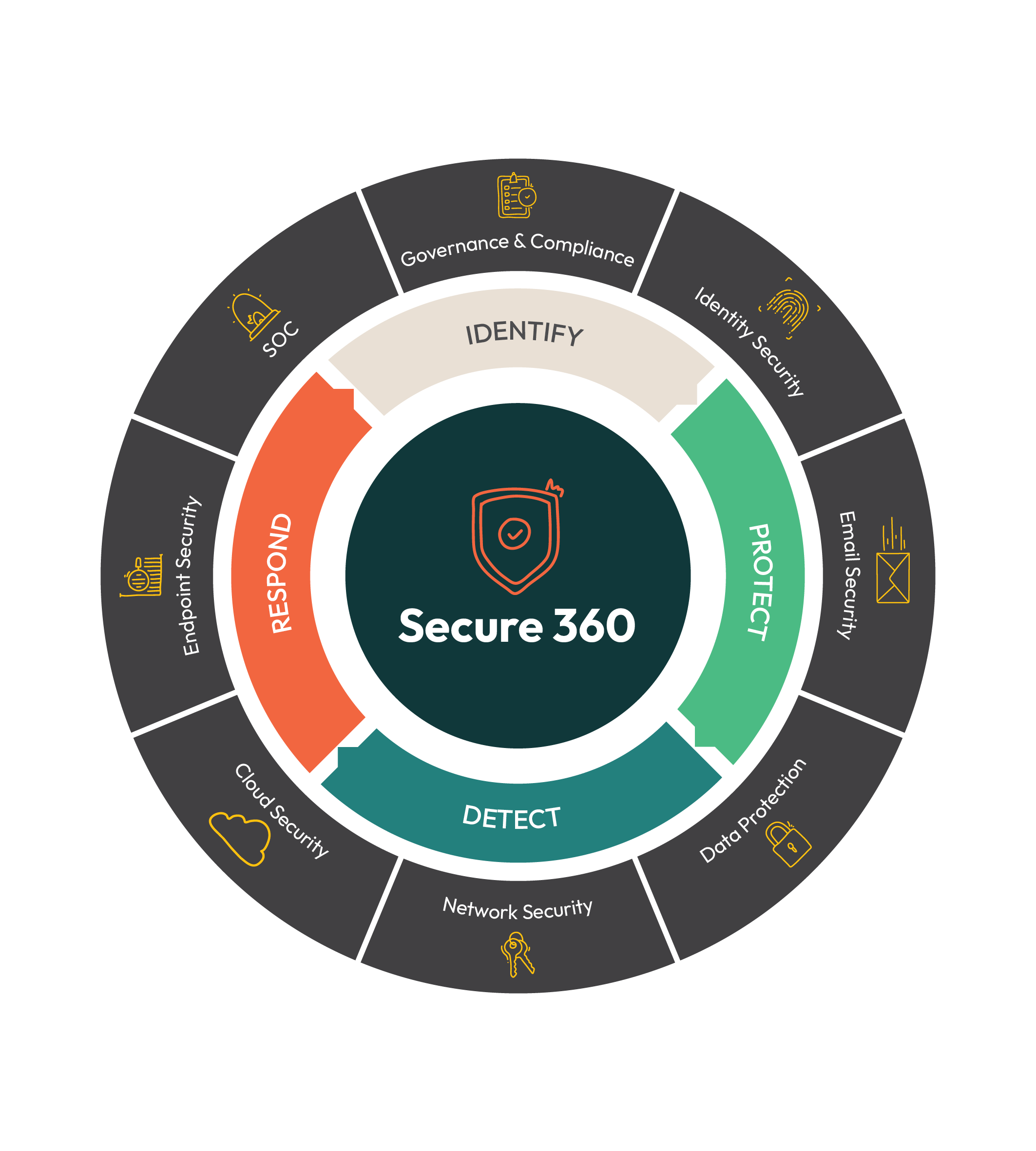
Navigating industry regulations can be challenging. We streamline the process by guiding you through every aspect of cybersecurity compliance, from Essential 8 assessments to PCI requirements. Our expert consultants deliver tailored strategies to help your organisation meet all necessary regulatory standards.
Our services include:
As identity attacks become increasingly prevalent, safeguarding your organisation is more critical than ever. We recommend leveraging our managed identity services and conducting a thorough identity risk review assessment to identify any gaps in your current configurations. By enhancing security through multi-factor authentication and ongoing monitoring, you can ensure that only authorised users access sensitive information, significantly reducing potential risks.
Email remains a significant vector for cyber attacks, making strong protection critical. Our managed email security services offer a layered defence approach, integrating advanced behavioural detection to identify and stop threats before they reach your inbox. Regular and automated phishing simulations help your team improve their ability to recognise suspicious emails, particularly across platforms like O365 and G Suite. Ensure that your email communication is secured against evolving threats.
In today’s complex digital landscape, comprehensive data protection is essential. With advanced tools for Data Security Posture Management, businesses can ensure robust security and compliance, safeguarding their sensitive and critical data. These solutions provide the necessary capabilities to protect valuable information, maintain regulatory compliance, and mitigate risks, allowing organisations to stay ahead of evolving threats and maintain a strong security posture.
Our managed network security solutions provide comprehensive protection for modern digital infrastructures. We establish a strong first line of defence by leveraging advanced perimeter security, including firewalls and Network Access Control. Web Application Firewalls protect critical applications from cyber threats. Our Secure Access Service Edge integrates network optimisation and security to provide seamless access, while SDWAN enhances network performance and reliability across distributed environments. Together these deliver a flexible, high-performing, and secure network, safeguarding your organisation from evolving threats.
As cloud adoption accelerates, ensuring the security of cloud environments is crucial. Modern cloud security solutions provide comprehensive monitoring, proactive vulnerability management, and stringent access controls to safeguard infrastructure and applications. By leveraging advanced technologies, organisations can protect cloud-native environments and ensure secure access with Zero Trust principles. These solutions enable businesses to maintain visibility, control, and security across their entire cloud ecosystem, providing resilience against evolving threats.
In an increasingly complex threat landscape, adopting Extended Detection and Response (XDR) is essential for enhancing your security posture. Secure Agility’s XDR solution integrates advanced threat detection, response, and remediation across your entire IT environment. By providing unified visibility and context, XDR enables faster identification of sophisticated threats, reducing the time to respond. Our proactive approach empowers your organisation to stay ahead of potential risks, ensuring comprehensive protection against evolving cyberattacks.
As cyber threats continue to evolve, having a robust Security Operations Center (SOC) is essential for effective defence. Secure Agility’s SOC, powered by Arctic Wolf, offers end-to-end security management for your business. With 24/7 monitoring, centralised log collection, and a dedicated concierge team, we proactively strengthen your security posture. This comprehensive service ensures you’re always protected, empowering you to meet your security goals with confidence and peace of mind.

We tailor our services to meet your business objectives
Let us manage the complexities of cyber security, so you can focus on what matters most – your business
Our team is always here to help! Offering continuous monitoring and rapid detection and response to keep your operations secure
Jul 26, 2024
Jul 12, 2024
Oct 13, 2022
Sep 2, 2022
Apr 22, 2022
Feb 28, 2022
Jan 14, 2022
May 21, 2021